Gsm Key Generation And Encryption
Encryption in the GSM network utilizes a Challenge/Response mechanism. Vmware vcenter license key generator. The Mobile Station (MS) signs into the network. The Mobile Services Switching Center (MSC) requests 5 triples from the Home Location Register (HLR). The Home Location Register creates five triples utilizing the A8 algorithm. Feb 23, 2013 GSM networks utilize encryption for three purposes: Authentication Encryption Key generation 13. The GSM network authenticates the identity of the subscriber through the use of a challenge-response mechanism. A 128-bit random number (RAND) is sent to the MS. How Do Authentication and Key generation work in a GSM network? Encryption in the GSM network utilizes a Challenge/Response mechanism. The Mobile Station (MS) signs into the network.
- GSM Tutorial
- GSM Useful Resources
- Key of the end user) generally robust, but a few successful attacks have been reported: – faked base stations – cloning of the SIM card GSM and UMTS security 8/11 3GPP security design principles Reuse of 2nd generation security principles (GSM): – Removable hardware security module.In GSM SM:I cdra.
- Jul 19, 2016 Key pair generation on Android app; Public key encryption on server ( uses RSA algorithm) and encoding cipher to QR code using PHP; QR code decode and decryption of cipher to get the secret generated by the server 1. Key pair generation on Android appWe mainly use 'spongy castle' as our default security provider. It's an alternative to default.
- Selected Reading
GSM is the most secured cellular telecommunications system available today. GSM has its security methods standardized. GSM maintains end-to-end security by retaining the confidentiality of calls and anonymity of the GSM subscriber.
Jan 04, 2018 DES algorithm follows the Feistel Structure Most of the Block cipher algorithms follows Feistel Structure BLOCK SIZE - 64 bits Plain Text No. Of Rounds - 16 Rounds Key Size - 64 bits Sub Key Size. Jun 24, 2015 Three algorithms have been specified to provide security services in GSM. A3 is used for authentication, A5 for encryption, and A8 for the generation of a cipher key 6. For authentication, the VLR sends the random value RAND to the SIM. The MS sends back the SRES generated by the SIM; the VLR can now compare both values.
Temporary identification numbers are assigned to the subscriber’s number to maintain the privacy of the user. The privacy of the communication is maintained by applying encryption algorithms and frequency hopping that can be enabled using digital systems and signalling.
This chapter gives an outline of the security measures implemented for GSM subscribers.
Mobile Station Authentication
Key Generator
The GSM network authenticates the identity of the subscriber through the use of a challenge-response mechanism. A 128-bit Random Number (RAND) is sent to the MS. The MS computes the 32-bit Signed Response (SRES) based on the encryption of the RAND with the authentication algorithm (A3) using the individual subscriber authentication key (Ki). Upon receiving the SRES from the subscriber, the GSM network repeats the calculation to verify the identity of the subscriber.
The individual subscriber authentication key (Ki) is never transmitted over the radio channel, as it is present in the subscriber's SIM, as well as the AUC, HLR, and VLR databases. If the received SRES agrees with the calculated value, the MS has been successfully authenticated and may continue. If the values do not match, the connection is terminated and an authentication failure is indicated to the MS.
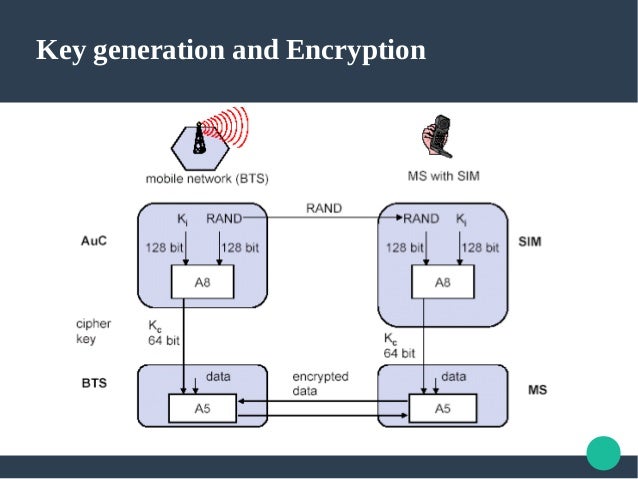
The calculation of the signed response is processed within the SIM. It provides enhanced security, as confidential subscriber information such as the IMSI or the individual subscriber authentication key (Ki) is never released from the SIM during the authentication process.
Signalling and Data Confidentiality
The SIM contains the ciphering key generating algorithm (A8) that is used to produce the 64-bit ciphering key (Kc). This key is computed by applying the same random number (RAND) used in the authentication process to ciphering key generating algorithm (A8) with the individual subscriber authentication key (Ki).
GSM provides an additional level of security by having a way to change the ciphering key, making the system more resistant to eavesdropping. The ciphering key may be changed at regular intervals as required. As in case of the authentication process, the computation of the ciphering key (Kc) takes place internally within the SIM. Therefore, sensitive information such as the individual subscriber authentication key (Ki) is never revealed by the SIM.
Encrypted voice and data communications between the MS and the network is accomplished by using the ciphering algorithm A5. Encrypted communication is initiated by a ciphering mode request command from the GSM network. Upon receipt of this command, the mobile station begins encryption and decryption of data using the ciphering algorithm (A5) and the ciphering key (Kc).
Gsm Key Generation And Encryption Download
Subscriber Identity Confidentiality
Gsm Key Generation And Encryption Key
To ensure subscriber identity confidentiality, the Temporary Mobile Subscriber Identity (TMSI) is used. Once the authentication and encryption procedures are done, the TMSI is sent to the mobile station. After the receipt, the mobile station responds. The TMSI is valid in the location area in which it was issued. For communications outside the location area, the Location Area Identification (LAI) is necessary in addition to the TMSI.